HTTP vs HTTPS: What Network Sniffers Can Really See

Have you ever wondered what someone on the same network could actually see when you’re browsing the web? You’ve probably heard that “HTTP is unsafe” and that “HTTPS keeps you secure,” but it still exposes some metadata. Have you ever really seen this in action?
In this blog, I’ll show you exactly what an on-network observer can capture. Using a small, ethical lab with Bettercap, I explored what’s visible when visiting websites from my own devices (a Kali VM as the attacker and my Windows PC as the victim) on a completely isolated network. You might be surprised at what can be seen, even without breaking any laws.
Understanding packet sniffing
Packet sniffing is the practice of observing network traffic to learn about devices and their communication. When traffic is unencrypted, it is possible to see the exact data exchanged. When traffic is encrypted, you can still see some metadata such as which websites or services are being contacted. Packet sniffing is a key concept in understanding network security and privacy.
Tools used (Bettercap-focused)
Bettercap: used to discover hosts and observe network level metadata from an attacker perspective.
My Windows PC: used as the test victim.
Note: this post intentionally does not publish commands or scripts to intercept traffic on networks you do not own. If you want detailed lab notes for private study, contact me for sanitized access.
Project workflow
I ran Bettercap on the attacker machine and open the help menu, you will see multiple modules. For this demo I focused on three high-level modules:
net.probe: host discovery on the subnet (lists IPs and vendor info of devices on the local network).
arp.spoof: a module that can enable a Man-in-the-Middle scenario in a controlled lab to show how traffic might be hijacked.
net.sniff: captures packets and extracts application layer metadata.
Observations
During the lab, I tested both HTTP and HTTPS websites to see what Bettercap can capture.
HTTP Example:
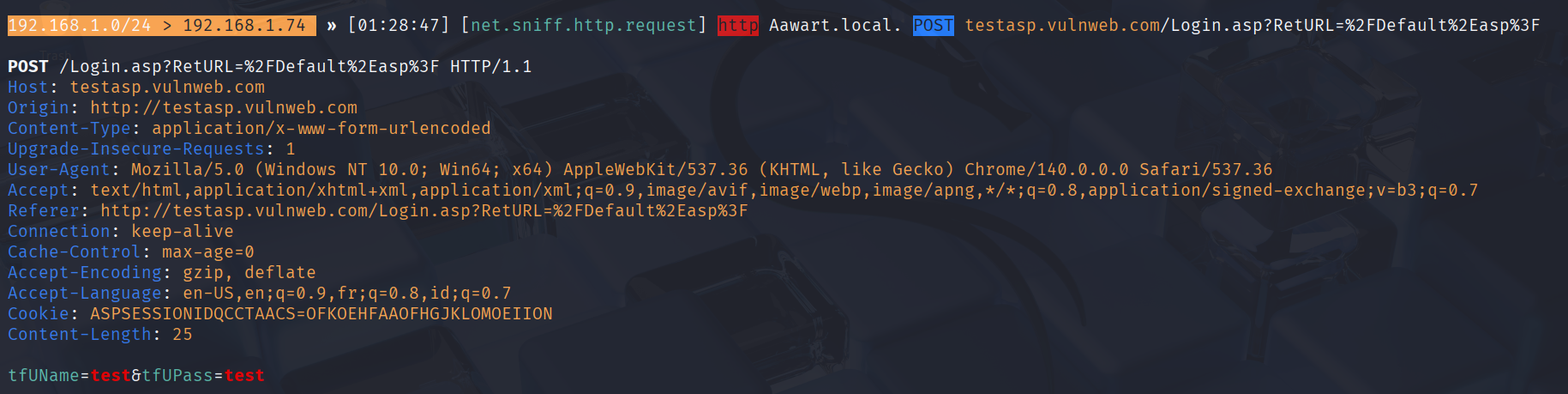
I visited http://testasp.vulnweb.com/ and went to the login page using:- Username: test
- Password: test
Bettercap captured exactly what I typed in the login form, including the username and password.
This clearly demonstrates that HTTP traffic is not encrypted and everything is visible to an on network observer.
Image: Bettercap captured username and password on HTTP site.HTTPS Example:
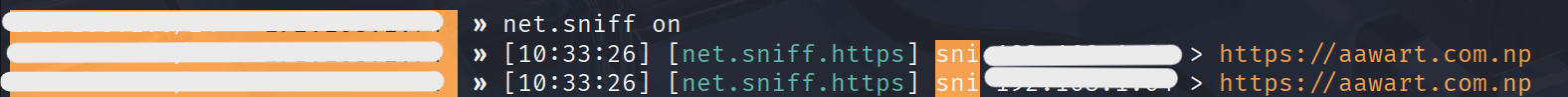
I visited https://aawart.com.np.
Bettercap could not see the login credentials or page content, but it still detected metadata:- TLS SNI: shows the domain
aawart.com.np - mDNS traffic: background protocol traffic that may appear in the capture

Image: Bettercap shows domain accessed via TLS SNI.- TLS SNI: shows the domain
Key Takeaways
- HTTP is dangerous: Everything is sent in plaintext. Usernames, passwords and page content can be captured by anyone on the same network.
- HTTPS is safer but not perfect: While login credentials and content are encrypted, metadata like the domain name (via TLS SNI) is still visible.
- Public Wi-Fi is risky: Any untrusted network can allow attackers to sniff traffic and steal sensitive information if sites are HTTP.
- Filtering helps: When analyzing captures, filtering out background protocols (mDNS, SSDP, etc.) improves clarity and focuses on meaningful activity.
- Ethics matter: Experiments should only be run on networks and devices you own or have explicit permission to use. Unauthorized interception is illegal.
Conclusion
This lab demonstrates how network traffic can be observed safely for educational purposes. Key lessons:
- Never use HTTP for sensitive activity on public or untrusted networks.
- Always prefer HTTPS to protect credentials and data, but remember that some metadata like visited domains is still visible.
- Understanding network security helps protect against attackers, especially on shared networks like coffee shop Wi-Fi or airports.
For anyone interested in a deeper look at this lab, I can share sanitized lab notes or a private demo under controlled access.
- Title: HTTP vs HTTPS: What Network Sniffers Can Really See
- Author: Aawart K C
- Created at : 2025-09-21 21:00:00
- Updated at : 2025-09-22 11:48:50
- Link: https://blog.aawart.com.np/Network_sniffing/
- License: This work is licensed under CC BY-NC-SA 4.0.